S3 API audit logs
S3 API audit logs keep detailed records of activity in the Lyve Cloud console as well as S3 API operations. To enable S3 API audit logs, you must select buckets to be logged from the target buckets available in the account. See the Example of S3 API audit logs.
Example of S3 API audit logs
The following is an example of an S3 API audit log file.
{
"serviceAccountCreatorId":
"john.doe@email.com",
"auditEntry":
{
"api":
{
"name": "PutObject",
"bucket": "bucket-1",
"object": "values-v2.yaml",
"status": "OK",
"statusCode": 200,
"timeToResponse": "2246401314ns" },
"time": "2021-01-22T10:49:30.699378337Z",
"version": "1",
"requestID": "165C883E70C2A5D0",
"userAgent": "aws-sdk-java/1.12.25 Linux/4.15.0-135-generic OpenJDK_64-Bit_Server_VM/11.0.12+7 java/11.0.12 vendor/Oracle_Corporation cfg/retry- mode/legacy",
"remotehost": "127.0.0.1",
"deploymentid": "ef46b1cb-6be1-4aa2-9c14-e7ffbc11986b",
"requestHeader":{
"User-Agent": "aws-sdk-java/1.12.25 Linux/4.15.0-135-generic OpenJDK_64-Bit_Server_VM/11.0.12+7 java/11.0.12 vendor/Oracle_Corporation cfg/retry-mode/legacy",
"X-Amz-Date": "20210122T104928Z",
"Content-Type": "text/yaml",
"Authorization": "AWS4-HMAC-SHA256 Credential=AHPEVYIPHVQ3XNOY/20210122/us-east-1/s3/aws4_request, SignedHeaders=content-type;host;x-amz-content-sha256;x-amz-date, Signature=<redacted>",
"Content-Length": "5637",
"X-Amz-Content-Sha256": "UNSIGNED-PAYLOAD",
"X-Amz-Server-Side-Encryption": "AES256" },
"responseHeader":{
"ETag": "219857b61eb0c3dc9a3916a0992fc803",
"Vary": "Origin",
"Server": "LyveCloud/DEVELOPMENT.2020-06-22T03-43-44Z",
"Accept-Ranges": "bytes",
"Content-Length": "0",
"X-Amz-Request-Id": "165C883E70C2A5D0",
"X-Xss-Protection": "1; mode=block",
"Content-Security-Policy": "block-all-mixed-content",
"X-Amz-Server-Side-Encryption": "AES256"
}
},
"serviceAccountName": "serv-acc-01"
}
The following table describes the parameters specified in the S3 API audit log file.
Parameter name | Description |
|---|---|
| A user who created the service account. |
| Specifies the API name. |
| Specifies the bucket name. |
| Specifies the object name. |
| Specifies the HTTP status. |
| Specifies the HTTP status code. |
| Time for the entire request to complete. |
| The timestamp in UTC zone. |
| Represents the current version of Audit Log structure. |
| A unique request identifier. |
| Specifies the User-Agent request header |
| Displays IP address of the client who sent the request |
| A unique deployment identifier. |
| Specifies the request header content. |
| Specifies the response header content. |
| Displays the name of Service Account associated with buckets. |
On the left-hand menu, select Settings.
On the Audit Logs Settings page, set S3 API Audit Logs to ON to begin saving audit logs.
On the Audit Log Target Bucket dialog, select the target bucket from the list to store the logs.
Set the target bucket only if you are setting the target bucket to write audit logs for the first time. However, if you have already set the target bucket while enabling console audit logs, you are not forced to select the target bucket.
Note
Only the buckets that are immutable are displayed in the list.
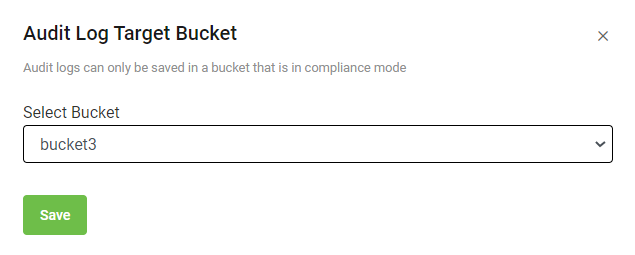
Select Save.
After you enable the S3 API audit log:
To change the target bucket:
On the Audit Log Settings page, a new section Audit Log Target Bucket is displayed. This section displays the target bucket name and bucket region. To change the target bucket, see Editing audit log target bucket.
To set the S3 API audit logs.
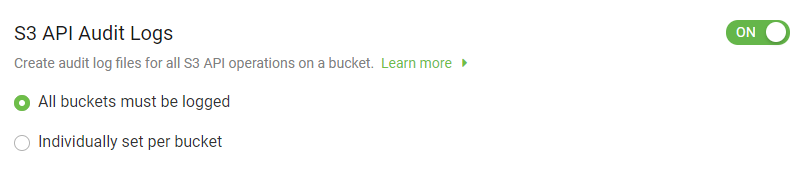
Select which buckets will have audit log.
All buckets must be logged: Selecting this option allows you to set and enforce logging for all available buckets in the account. By default, this option is selected.
Individually set per bucket: Selecting this option allows you to edit each bucket to enable logging manually.
Note
The All buckets must be logged and Individually set per bucket options are available only after you enable S3 API audit logs, and the target bucket is set to store logs.
After selecting the Individually set per bucket option, you must choose each bucket individually and then enable the S3 API audit logs. To enable S3 API audit logs for an individual bucket, see Editing bucket properties. Once S3 audit logs are enabled, the selected bucket in the account is labeled as Logged.
Disabling S3 API audit logs
While enabling S3 API Audit Logs, if you select the Individually set per bucket option and later disable audit logs, the S3 API Audit Logs option will be unavailable in that individual bucket.
On the left-hand menu, select Settings.
On the Audit Log Settings page, set S3 API Audit Logs to Off.
After you switch off S3 API audit logs, the Logged label is removed from all buckets.